Recently, I've been looking and reading articles about Arduino UNO R3. Search from Aliexpress awhile, and i decided to buy a cheap Arduino UNO R3 clone to play around with. After waited for 2 weeks plus, i finally get the board which look similar to this with the word "UNO" only, instead of "DCcEle DCcduino UNO":
First of all, setting up the environment :
1. Download and install the USB-Serial Driver. Saw from the chip surface, mine is using a "WCH CH340G", therefore, need to download the drive and setup separately :
Driver for Arduino Clone with WCH CH340G
2. Setup and configure Arduino IDE
- Run into problem while running the Zip version of the IDE at first. Now, it run well after configured the "sketchpath" in "preferences.txt" located in the "lib" folder
After everything is set, and when i plug in the board, all i found is that i can compiled and verified my "Hello World" sketch successfully, but, the upload is unsuccessful. After a few digging, finally found the solution for it :
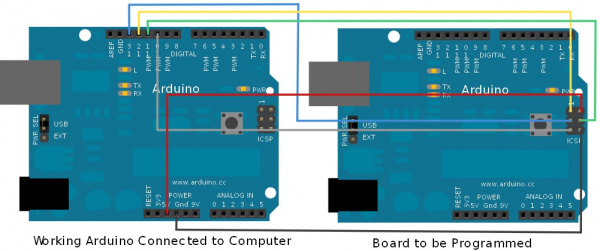
- Luckily, i have a friend with a working UNO R3. Therefore i am using his Arduino UNO R3 as ISP.
- First i open the example sketch "ArduinoISP" provided inside the IDE.
- Upload the sketch into my friend's working board.
- I connect my board as following :
- Select "Arduino as ISP" as programmer
- Select the serial port for the working Arduino
- Press "Burn Bootloader"
Magic Happen... it seem like my cheap Arduino UNO R3 i bought from Aliexpress is not loaded with bootloader. And now, it's work flawlessly.
.








.jpg)
